Secure video playback like Netflix, Disney+
26 February 2025
@Bibhabendu MukherjeeInsights into the Video playback mechanism , how platform like Netflix, Disney+ secure their video content from piracy
Imagine you’re watching your favorite show on Netflix. You hit play, and within seconds, high-definition video streams seamlessly to your screen. But have you ever wondered—why can’t someone just copy this video and share it for free? Or why does screen recording fail when you try to capture premium content?
Behind the scenes, a highly sophisticated security system is at work, using hardware-backed Trusted Execution Environments (TEEs) and Digital Rights Management (DRM) to prevent piracy and content theft.
Online piracy is a multi-billion dollar problem. Without strong protection, anyone could rip high-quality movies and shows, making them available illegally.
But companies like Netflix, Disney+, and Amazon Prime use a powerful security system that operates beyond software-level encryption—a hardware-based Trusted Execution Environment (TEE) that ensures even the device’s own OS cannot access decrypted video data.
Option 1: How Normal Video Playback Works Without DRM or TEE
The user selects a video on a streaming website/app (e.g., a non-DRM YouTube video), request is sent to the video server. The server sends the unencrypted (raw) video file over HTTP/HTTPS. No DRM or decryption process is needed, HTTPS is not used, attackers can intercept the stream (MITM Attack).
The video file is stored in temporary cache (RAM or disk)*. The CPU/GPU renders the video onto the screen
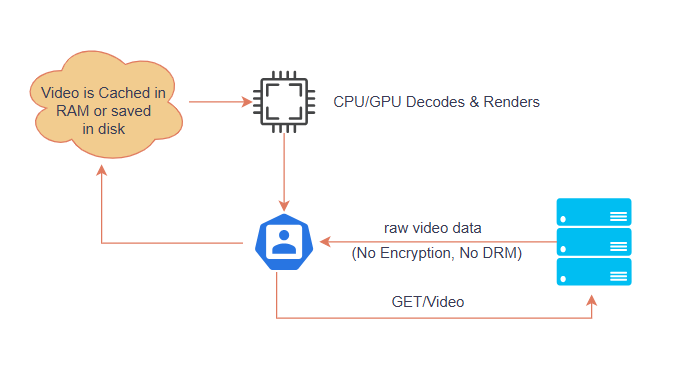
* Since no TEE or DRM exists, hackers can extract the video from cache
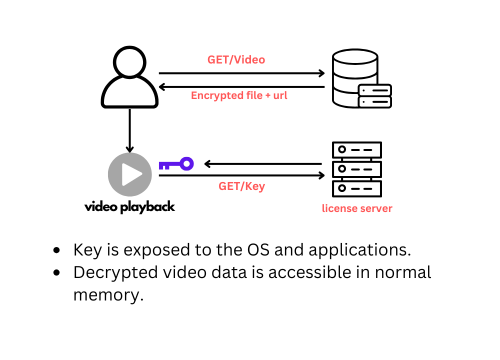
Option 2: Clear key encryption techniques
In clear key encryption without TEE, the decryption process is less secure because the key and decrypted content are exposed to the device’s main memory.
When a user requests DRM-protected video, the encrypted video and a key request URL are sent.The video player fetches the decryption key from the license server after validation. Since there’s no TEE, the key and decrypted data are handled in normal memory, making them vulnerable to interception and piracy.
How Netflix Blocks Screen Recording & Piracy
- Encrypted Video Streaming – Netflix never sends raw video; it is always encrypted before reaching your device.
- Secure Decryption Using TEE – The decryption key is stored in a Trusted Execution Environment (TEE) like Secure Enclave (Apple) or Widevine DRM (Android/Chrome), making it impossible to extract.
- Secure Video Path (Hardware Protection) – The decrypted video is sent directly to the GPU/display through a protected memory path, bypassing software-level access. This prevents screen recording tools from capturing frames.
- Screen Recording & Debugging Detection – Netflix detects screen recording tools (e.g., OBS, Xbox Game Bar) and blackens the screen if they are active.